- Google Cloud Security
- Security Command Center
- SCC Forum
- Using Event Threat Detection to Detect VMs in Unau...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In this community post, we’ll take a closer look at Event Threat Detection (ETD) in Security Command Center Premium, with a focus on the ability for customers to create custom ETD modules.
SCC Premium provides a framework for creating custom modules for ETD using module templates. In this post, we’ll take a closer look at using one of these templates to create a finding that is triggered when a user provisions a virtual machine in an unauthorized GCP region.
In Google Cloud, a region is a geographical location that can host resources. Regions are further divided into distinct deployment areas called zones, which ensures infrastructure redundancy within the context of a region. In GCP, resources that reside in a specific region, like compute instance VMs, are called regional resources.
SCC Premium administrators have the ability to detect the provisioning of VMs in specific regions and to trigger a finding based on that activity. Let’s take a closer look at how this is done.
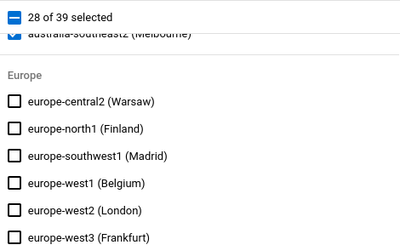
In this demo, we’ll configure SCC Premium to trigger a finding whenever a virtual machine is provisioned in any region located in Europe.
In SCC Premium select Overview, then select Settings. From the list of modules, select Manage Settings under Event Threat Detection.
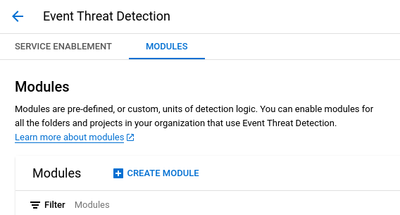
Select Modules on the next screen, then select Create Module to launch the custom ETD module creation workflow.
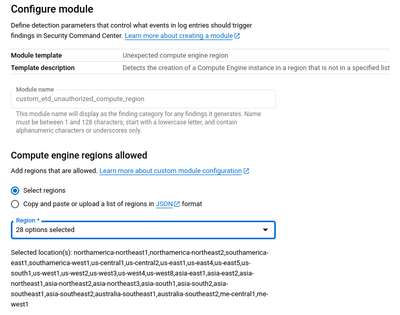
In this scenario, we’re creating a rule that is designed to trigger when a virtual machine is provisioned in any GCP region in Europe. For this reason we’ll select Compute Engine regions from the list of available templates.
Specify a name for the module. In the Region selection drop-down, we are asked to select all regions that are allowed, so in our scenario we will select all regions other than the regions in Europe.
Verify that the module name is correct and that the list of regions selected previously is accurate. Select Next.
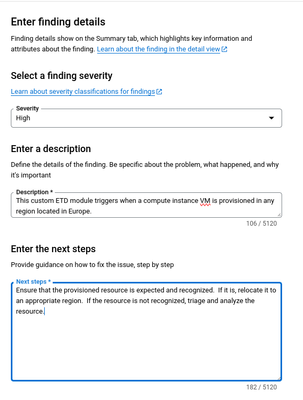
Specify a severity of High and populate the custom finding with additional metadata as shown below. Select Create to save the new custom module.
You can optionally test your custom ETD module by launching a compute instance VM in a region located in Europe. Note that doing so will incur costs associated with provisioning this compute engine resource, so in this post we’ll provision the resource as part of this demo and show what the associated finding looks like in SCC Premium.
We can then pivot back to SCC Premium and click Findings to see that our activity has triggered the custom rule we created earlier.
Since we manually triggered this finding as part of this scenario, we can select the finding and mute it.
Event Threat Detection in SCC Premium allows customers to create custom modules based on other types of templates as well, such as the assignment of specific IAM roles to principals, usage of specific compute images as part of provisioning a compute instance, and more. For more information about ETD, please see our overview.
-
Attack Path Simulation
2 -
Automations
2 -
Compliance
2 -
CSPM
2 -
ETD
6 -
Findings
14 -
Integration
3 -
Log
3 -
Notifications
2 -
Reporting
5 -
SCC Enterprise
3 -
SCC Premium
3 -
Security Command Center
2 -
Threats
10 -
Vulerabilities
4 -
Vulnerabilities
1
- « Previous
- Next »

 Twitter
Twitter