This website uses Cookies. Click Accept to agree to our website's cookie use as described in our Privacy Policy. Click Preferences to customize your cookie settings.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Google Cloud Security
- Chronicle
- Articles & Announcements
- News & Announcements
- SecOps Customer Newsletter - July 2023
Topic Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Solved

Post Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Reply posted on
--/--/---- --:-- AM
Post Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hello SecOps Community,
Stay up to date with everything going on in Chronicle SIEM and SOAR by reading the SecOps Customer Newsletter! Updated every other month, you can find a summary of major Product Updates, Learning and Training, Community Announcements, Best Practices, and Upcoming Events.
Chronicle Security Operations Updates
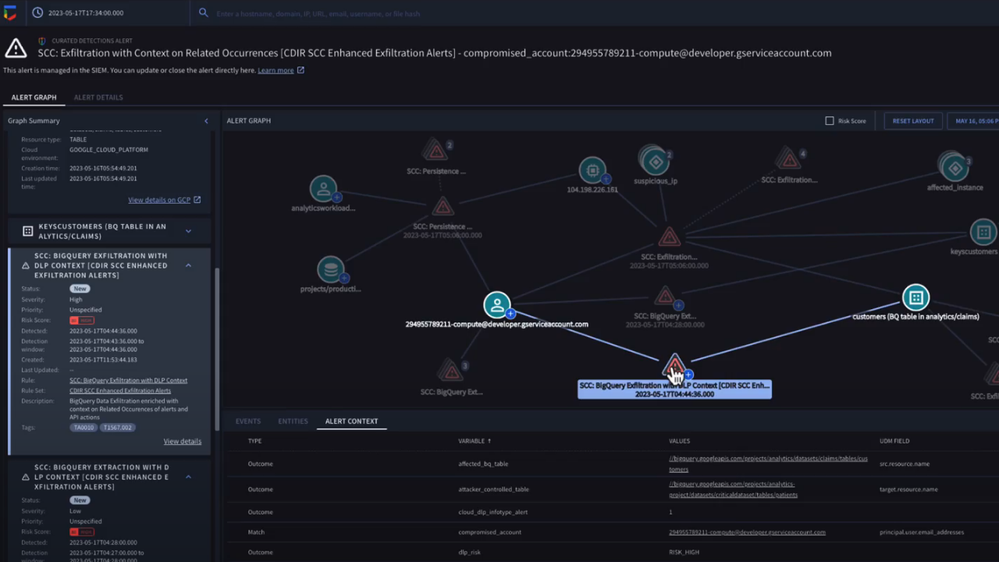
Introducing turnkey TDIR (Threat Detection, Investigation and Response) for Google Cloud
This latest release enables teams to:
- Detect with confidence. Out-of-the-box detection rule sets developed by Google threat researchers surface cloud attack vectors and provide high fidelity, contextualized alerts that quickly give insight into potential threats in your Google Cloud environment.
- Investigate with full context. Visualize threat storylines, complete with cloud-specific context that is correlated with additional data and context from across your environment for fast and efficient investigations.
- Respond with speed and precision. Streamline workflows and automate response actions with prebuilt playbooks and best practices designed specifically for Google Cloud. Chronicle SOAR’s case management and team collaboration help ensure fast and timely response.
- Simplify data ingestion. Chronicle automatically ingests, normalizes and contextualizes cloud telemetry from a variety of Google Cloud services (such as Cloud Asset Inventory, Google Kubernetes Engine, Google Compute Engine, cloud audit logs, and Cloud DLP), reducing the need for complex and time-consuming engineering.
Check out our Security Summit session or read the blog to learn how we provide superior, packaged TDIR for Google Cloud at a fraction of the effort.
Aggregations & Statistics Available in Search
- Quickly answer a wide range of new questions leveraging our search cache on up to 1M events.
Exclusion Filtering for Curated Detections
- Quickly and easily filter out noisy or unwanted detections from your curated detection results.
Revamped Alert View in Chronicle SIEM
- Clearly differentiate between the alert investigation and the audit area with “Overview” and “History” tabs.
- Quickly access and pivot to more alerts associated with your detection rule via a new button in the detection widget, “view other alerts from this rule.”
- Prioritize high-risk and critical security findings with expanded columns including risk score and tags in the alert list.
- Customize columns in the alert list to explore different triage scenarios.
- Enable more complex filtering scenarios by expanding filters to include OR and AND operators.
Customer Onboarding Portal
- Easily create your own Chronicle SIEM instance, review service account configurations and configure SSO settings.
- Access self-service tooling for BYOP and BYOID and self-migrate to Chronicle’s expanding set of GCP-centric capabilities.
- Contact your CSM for more information.
To find a comprehensive list of recent Chronicle Release Notes/Changes, go here.
Chronicle Security Operations Best Practices
Check out our latest blogs that help teams leverage Chronicle for more effective threat detection, investigation and response:
- New to Chronicle: First and Last Seen: Lean into the scale of Chronicle to build detections around the derived context of “first and last seen” across file hashes, domains, IP addresses, users and assets.
- New to Chronicle: Grouped Fields: Explore your data by building searches where the values of interest are source or destination using “Grouped Fields”.
- A Look Back at Curated Detections: Chronicle’s collection of rules covering a range of critical threats continues to grow covering more threats and introducing a set of powerful features customers can use to build their own detections.
SecOps Events, Training, and Content
- Craving better security outcomes but not quite ready to ditch your legacy SIEM? - Join the Twitter Spaces discussion to learn what SIEM augmentation can do for you.
- What you need to know: 2023 State of Cloud Threat Detection and Response - Watch this on-demand webinar to explore the insights from our recent survey, including the main challenges and opportunities for SecOps teams as they transform to a cloud-first threat detection and response mindset, and see what your peers had to say.
- Simplify End-to-End Threat Detection, Investigation and Response in the Cloud - Check out our latest webinar on how TDIR in the cloud differs from traditional on-premises approaches, building end-to-end workflows that work for you, and operationalizing this in Chronicle.
0 REPLIES 0
Top Labels in this Space
-
AI
1 -
Alerts
1 -
Block
1 -
Chronicle
28 -
Community Edition
2 -
Connector
2 -
Integrations
1 -
Mandiant
2 -
Newsletter
2 -
Office Hours
4 -
Placeholder
1 -
Playbook
1 -
SecOps
2 -
SIEM
2 -
Siemplify
5 -
SOAR
1 -
Toast of the Town
3 -
Use Cases
1 -
Webinar
1
- « Previous
- Next »

 Twitter
Twitter